Today marks the death of one of our most beloved friends, Robin Klauss, at the heartbreaking age of 29. I remember clearly when, during one of our countless karaoke nights which were usually filled with joy and laughter, she revealed the news of her cancer diagnosis. During the previous weeks, she had noticed a small bump on the back of her neck, which she thought might be a spider bite. But the bump wouldn’t go away, and eventually she started noticing a decrease in mobility in her neck and arm. After a visit to the doctor, she was told that it’s not a spider bite, but cancer – a tumor in her neck that had already begun to invade her vertebrae and spinal cord.
During her experience with cancer, she wrote a few brief posts on her LiveJournal account, which I thought I’d re-post here, since that account is obviously no longer maintained, and will likely be shut down eventually. Here are the posts in chronological order (take note of the startlingly fast progression of the disease):
Jun. 18th, 2008
I’ve been diagnosed with adenocarcinoma of an unknown primary. Being an unknown primary it’s automatically labeled stage IV. Thought you might like to know.Jun. 19th, 2008
My throat hurts so bad from the radiation. I feel like there’s this giant scab on the back of my throat and that I’m swallowing steel wool. The radiation oncologist that is on-call tried to call in a prescription for some kind of numbing something or-other but the pharmacist doesn’t have the lidocaine or whatever to mix it. 🙁 I tried to use chloroseptic spray but I couldn’t get it far enough back (and it tastes like shit). I so fucking hate this.Jul. 2nd, 2008
So, today I had my 1 month follow up after the radiation surgery. On the bright side, all three of the docs I saw today were ecstatic about my progress. The neuro-oncologist about fell out of her chair when she was my arm movement was back. She said I am “the poster child for stereo-tactic radio-surgery.” 🙂 No chemo yet. 🙂 I have another follow up in 2 months to see how the tumor is doing. So, if it’s still there, then maybe chemo? No clue. I am having some pain at the top of my head on the right side. My medical oncologist said to keep an eye on it and let him know if it gets worse or if I notice any new pain. The main goal is to keep an eye out for any new metastases. However, the pain I’m having on my left side may be due to how the tumor destroyed the C3 and C4 vertebrae. There may be instability in my neck and the ligaments may have relaxed. Whatever that means. My neuro-oncologist ordered 6 x-rays of my neck and will be presenting my case to a spinal tumor board tomorrow to see if other doctors and neurosurgeons think I should have surgery on my neck to help stabilize it. The last thing I want is surgery and to miss work, however, I am also completely terrified that I will crack my neck because of how fragile it is. I doubt I’ll find out what she has to say tomorrow, hopefully on Monday.Jul. 15th, 2008
Yesterday I had an appointment with a neurosurgeon regarding strengthening my neck. First, and most importantly, he was really hot. His PA wasn’t bad looking, either. Lucky me! Second, I need to have neck surgery next Friday, July 25. He said the when the cancer invaded my C3 and C4 vertebrae, it replaced bone with cancer. So now my neck is slowly collapsing to the right side and fracturing because there’s nothing there to support it. Surgery doesn’t have to be done ASAP but much sooner rather than later. Basically, if I don’t have the surgery, my neck will break. He said something about putting mesh cages and bone graft or something in the destroyed vertebrae. There will be two incisions, one in the front, then they’ll flip my fat ass over and then another in the back. I don’t know how big the front incision will be but he said the back will be about 4″. I’ll spend 5-6 days in the hospital and about a week in rehab and then recover for 2-4 more weeks. Yup. I’m a lucky girl!Aug. 1st, 2008
I had the surgery last Friday. The surgery itself was over 11 hours long. They wheeled me away at 7:30am and my parents didn’t get to see me again until around 9:00 that night. My mom said, for some reason, the surgery didn’t start until 9:30ish but I only remember them wheeling me away, asking me a couple of questions and being in the operating room for about 3 minutes and I can’t remember anything else. For some reason hot doc didn’t do the mesh cage thing he was talking about and instead did metal plates and screws. This will make it a blast to travel. I’ll be setting off metal detectors like a freakin’ terrorist. Okay, it won’t be that bad. He did say that the plates are not supposed to set off metal detectors but I will have some card to say that I have this stuff in my neck to get me out of jail. After surgery they checked my breathing and I wasn’t breathing on my own so the intubated me with a different/smaller kind of breathing tube and I was unconscious in ICU until they woke me up to extubate me on Sunday morning. They didn’t move me into a regular room until Monday afternoon and I was finally discharged Wednesday afternoon. I didn’t have to go to rehab because 1.) my pain is negligible and 2.) I’m moving surprisingly well. Hot doc took a bone graft from my right hip and, right now, that’s what hurts and makes life difficult. I freakin’ walk like Frankenstein’s monster because I have to take it easy. My throat is also killing me, not only because of the intubation, but also because of the surgery. Hot doc said he would have to move my esophagus aside to be able to get to the vertebrae and the pain is normal and should go away soon. It definitely is getting better every day but it still hurts like hell. I have to wear a neck brace at all times except when I shower or eat. I can’t bend or twist my head and no lifting anything over 10 pounds. I’m recovering at my parent’s house, where I’ll be for the next 5 weeks. 5 weeks! Agh! And I can’t drive because I can’t turn my head so I am literally depending on them for EVERYTHING! I feel like a 2 year old. My mom makes my food and does my laundry and they’re both there when I go for a walk because they need to be there in case I fall or something. Because the biopsy was so unclear, hot doc removed some of the tumor and sent it off to pathology. Hopefully it will tell us more about what kind of cancer this is and the best way to treat it. He definitely thinks chemo is a good idea, so that will be starting soon. Everyone keeps saying I shouldn’t be so sure that it will be the kind where I’ll lose my hair, but I’m pretty damn sure it will be. I wonder if bald is is this season? Also, I have to renew my driver’s license in September… What will it say under hair color? Bald?Aug. 24th, 2008
So nothing new has been happening. I was hoping to be back home this weekend but I’m still at my parent’s house. Hopefully I will be back in C-bus next weekend. The incision on the back of my head isn’t healing well. It seems like a couple of stitches popped before it was healed so now I have a hole in the back of my head. My dad said it’s slightly smaller than a dime but it’s not really healing. I saw my hot neurosurgeon on Tuesday because of it not healing. He had us put packing in the hole for a few days and now we’re doing this wet/dry thing where my mom has to clean the hole out with saline and then put dry gauze on it. We’re supposed to do it 4 times a day. He wants to see me again tomorrow and said that he didn’t want me to go back to work yet. I’ll find out tomorrow if he’ll let me go back to work next week. I really don’t mind seeing him again. He’s so freakin’ hot! He called me at my parent’s house yesterday morning to see how it’s healing. He really had to do some searching because I changed all of my phone numbers in my chart to be my cell, house and work numbers. I really have no clue where he got there number. And he said he wants to see me when I have my next oncologist appointment in September. Then I’ll also see him when I have my next follow up with him in October. I think he’s just smitten with me and he’s too shy to make his move. Okay. I’m delusional but it could happen, right?Sep. 8th, 2008
I went in for my three month follow up today. The tumor has grown 1 cm since the beginning of July and it looks like some new lymph nodes are involved. My oncologist wants me to have a PET scan to see if the lymph nodes are really involved with the cancer or if they’re just inflamed from the surgery. He offered me three options to deal with the cancer: 1) do nothing, which is not an option at this point, 2) some kind of clinical trial that involves one type of chemo, given once every three weeks, and a daily pill that is used to treat TB, 3) a chemo cocktail that is three different kinds of chemo given at once. The clinical trial will waste too much of my FMLA time. I only have about 5 weeks left. The trial is divided into 2 different phases for a total of 37 days straight. Out of those 37 days, I would need to be at the hospital for at least 13 of the days. That’s not including days that I feel too tired or whatever to go to work. Following the 37 days, it would be just chemo once every three weeks until my doc says it’s done. I don’t like the idea of wasting all of those FMLA days. That will leave me with about 12 days for chemo after the first 37 days and for days I don’t feel well or am too tired. My mom thinks I’m choosing work over my health but she fails to remember that it’s because of work that I have health insurance to pay for all of this. If I lose my job, I lose my health insurance. Also the chemo is only given on Mondays. That leave no time for me to recover before I have have to drive 2 1/2 hours back to Columbus. So I’m opting for the third choice, the three chemo cocktail. It’s also once every 3 weeks but it doesn’t require the time commitment the trail does. I am going to wait to get a second opinion. I want to see a doc at the James but I’m having a hell of a time getting in to see someone. I would much rather have chemo here and recoup at my place. My job this week is to be a pain in the ass and call every doc I know at the James to get someone to refer me to a medical oncologist. Hopefully I won’t be dicked around.Sep. 10th, 2008
I was able to find an oncologist at the James! I called someone, who talked to someone else and said, “Oh, yes, I remember talking to Carrie about you before. You mean no one ever called you to schedule an appointment?” *head desk* So I’m totally not going to go back to see that guy in Cleveland. It works out so much better for me to see the oncologist here. I have to take a whole day off work for a 30 minute appointment, versus just a couple of hours. And I’ve already seen a radiation oncologist and a neurosurgeon at the James who have said in the past that they would take care of my 3 month check-ups, if I want them to. What the Cleveland oncologist said is that this thing will never go away. We can only hope to decrease or maintain the size of it before it spreads further. Fantastic. With my birthday coming up it makes me wonder, how many more birthdays will I have?Sep. 24th, 2008
I finally got to see the new oncologist at the James today. He wants me to have a PET scan tomorrow and start chemo on Friday. When I told my mom and my co-workers everyone had the same look of “holy crap! so soon!” on their faces (well, in the case of my mom, she said it). It’s about time. I’m in so much pain. The pain killers I have stopped working so well last week. I hate taking them and I’m totally afraid I’m going to get addicted to them but I really do need them to function.
She didn’t do any more writing after that, likely because of the effects of the pain killers or the chemo. And of course we hardly saw her anymore because the medications and the pain kept her virtually immobile at home, and cared for by her family.
In her second-to-last post, Robin asks how many more birthdays she would get to celebrate (she had just turned 29). The answer turned out to be zero. The cancer would claim her life just over a year after the initial diagnosis. That’s the cruel, cold, indiscriminate nature of this disease. Once we get past the bewilderment of contemplating that this could happen to any of us, all we can do is cherish every moment we get with our friends and loved ones, and remember the happiness and warmth that Robin brought to our lives.
Here is Robin during a random night out, expressing what would later become her response to cancer:
 (taken from my crappy Motorola phone at the time)
(taken from my crappy Motorola phone at the time)
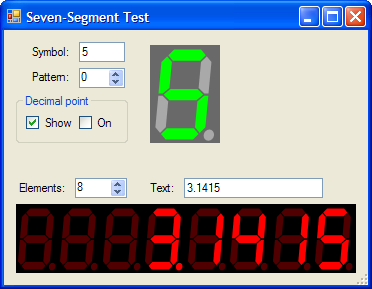 I’m usually not a big fan of custom controls except in the most extreme circumstances. From the point of view of usability, it should always make the most sense to use the controls that are shipped with the Operating System. Your user base is already familiar with the OS’s native controls, so creating custom controls would only add to the learning curve for your application. But I digress. Sometimes, there are certain controls that just beg to be written, whether they’re useful or not.
I’m usually not a big fan of custom controls except in the most extreme circumstances. From the point of view of usability, it should always make the most sense to use the controls that are shipped with the Operating System. Your user base is already familiar with the OS’s native controls, so creating custom controls would only add to the learning curve for your application. But I digress. Sometimes, there are certain controls that just beg to be written, whether they’re useful or not.